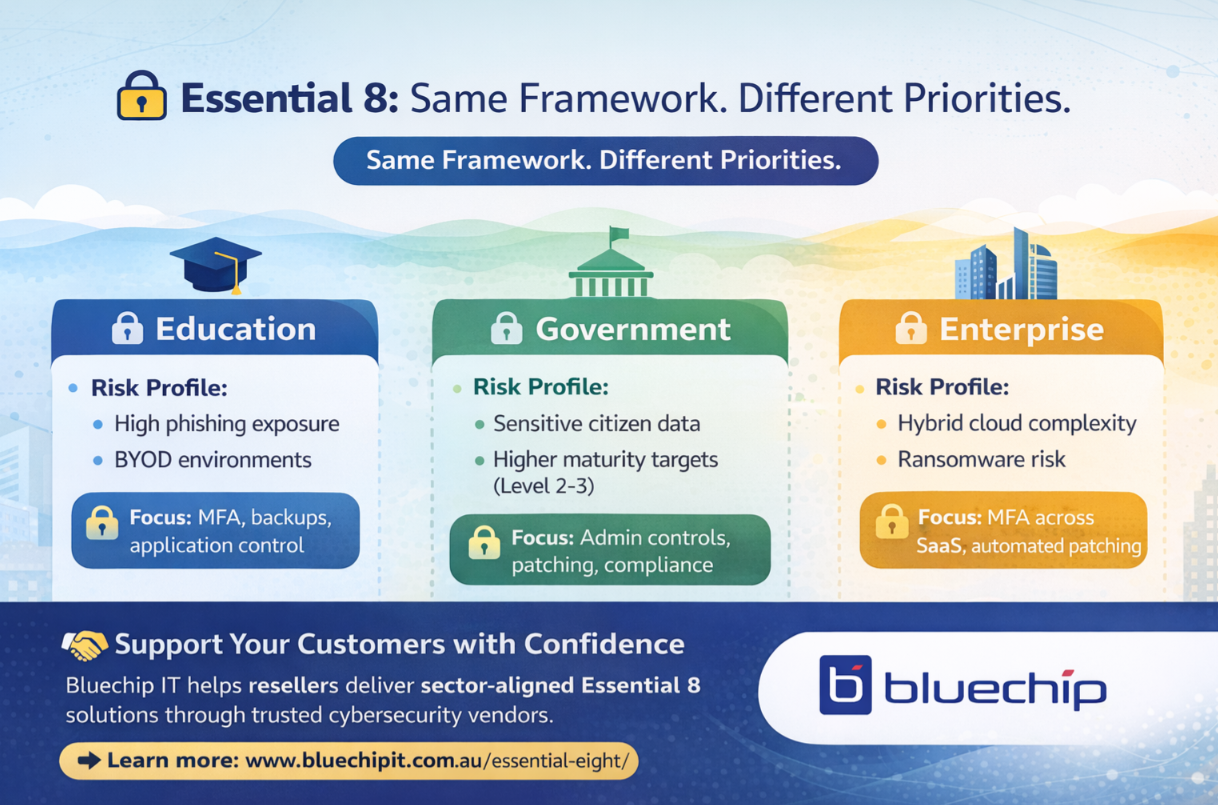
Cyber threats do not discriminate. However, their impact looks very different across sectors. A phishing attack in a school can disrupt learning. Meanwhile, a breach in government can expose citizen data. In enterprise, ransomware can stop operations overnight.
Because of this, many organisations are turning to the Essential 8 framework to strengthen their cyber posture. Developed by the Australian Cyber Security Centre, the Essential eight provides practical guidance to reduce common attack vectors.
At Bluechip IT, we support resellers and partners delivering Essential eight cyber security solutions across Australia. As a distributor with leading cybersecurity vendors, we help partners align solutions to sector-specific requirements without adding unnecessary complexity.
In this article, we explore how the Essential 8 applies differently to education, government, and enterprise, and what that means for Essential eight implementation in each environment.

A Quick Refresher — What Is the Essential 8?
The Essential 8 is a set of eight ASC mitigation strategies designed to reduce cyber risk. It forms the foundation of the essential 8 cyber security model used across Australia. The framework was developed by the Australian Signals Directorate. It focuses on practical controls such as patching, multi-factor authentication, and application control.
Importantly, the ASC essential 8 includes a maturity model. Organisations can measure themselves from Level 0 to Level 3. Each level reflects how consistently and effectively the controls are implemented. According to the ACSC Annual Cyber Threat Report 2022–23, the ACSC received over 94,000 cybercrime reports in one financial year. That equates to one report every six minutes.
Therefore, Essential eight cyber mitigation strategies are no longer optional. They are a baseline for resilience.
Why Sector Context Changes Essential Eight Implementation
The 8 essential controls remain the same. However, implementation priorities differ.
- First, data sensitivity varies. Government agencies manage classified or personal citizen data. Schools manage student records. Enterprises manage intellectual property.
- Second, operational impacts differ. A university outage disrupts thousands of students. Meanwhile, a government outage can halt public services.
- Third, regulatory oversight is stronger in some sectors. Government agencies often require higher maturity targets.
- Finally, the threat landscape shifts. Nation-state actors target the government. Ransomware groups often target enterprises. Phishing campaigns heavily target education.
As a result, Essential eight security must align with sector risk.
Essential 8 for the Education Sector
Key Risk Factors in Education
Education environments are highly distributed. They support students, staff, contractors, and researchers.
In addition, many institutions allow BYOD. This increases endpoint exposure. Budgets are often constrained. Therefore, IT teams must balance security with cost. Phishing remains a major threat. Students and staff frequently receive malicious emails.
Priority Essential 8 Controls for Education
Multi-Factor Authentication is critical. It reduces credential compromise. Application Control helps prevent unauthorised software. This is important in open environments.
User Application Hardening limits browser-based attacks. Meanwhile, Regular Backups ensure recovery after ransomware. However, many institutions struggle with patching cycles. Legacy systems in universities can delay updates. Inconsistent admin privilege control also creates risk.
For partners supporting schools or universities, a structured gap assessment is the best starting point.
At Bluechip IT, we help you identify sector-specific gaps and align vendor solutions accordingly.
[Request an Essential 8 Gap Assessment >>]
Essential 8 for Government Agencies
Why Government Faces Higher Maturity Expectations
Government agencies often aim for Level 2 or Level 3 under the Essential 8 ascs maturity model. This reflects higher risk exposure. They manage sensitive citizen data. In addition, they face nation-state threat actors. Therefore, Asc essential eight alignments are closely monitored.
Guidance from the Australian Cyber Security Centre sets clear expectations.
Controls That Require Strict Implementation
Application Control must be tightly enforced. Restricting Administrative Privileges is equally critical. Patch Operating Systems must occur within defined timeframes. Microsoft Office Macro Settings must block malicious code.
Compliance and Reporting Considerations
Government agencies require strong audit documentation. Evidence tracking is essential. Continuous monitoring supports ongoing compliance.
For resellers, this creates opportunity. However, it requires trusted vendor ecosystems and clear maturity alignment.
Essential 8 for Enterprise Organisations
Enterprise-Specific Risk Profile
Enterprise environments are complex. They include hybrid cloud, on-prem systems, and SaaS platforms. Third-party vendors add additional exposure. Therefore, Essential eight cyber controls must extend beyond internal networks.
Implementation Priorities
Multi-factor authentication across SaaS platforms is essential. Patch management automation improves speed and coverage. Backup resilience strategies must include immutable or offsite storage. This reduces ransomware impact.
Scaling Essential Eight Security Across Multiple Sites
Enterprises require centralised governance. Security operations must align with IT and risk teams. Vendor ecosystem integration becomes critical. This is where distribution partners add value. We help resellers combine technologies that support Essential eight implementation at scale.
Education vs Government vs Enterprise — Essential 8 Comparison
| Factor | Education | Government | Enterprise |
| Target Maturity | Level 1–2 | Level 2–3 | Level 1–2+ |
| Budget Constraints | Moderate | Funded but regulated | Variable |
| Threat Level | High phishing | Advanced persistent threats | Ransomware |
| Complexity | Distributed users | Highly regulated | Hybrid IT |
How to Approach Essential Eight Implementation Based on Your Sector
- First, conduct a gap assessment. This identifies maturity gaps.
- Next, determine your target level. Align this with sector expectations.
- Then, prioritise high-risk controls. Focus on quick wins first.
- After that, engage experienced Essential 8 partners. Vendor alignment matters.
- Finally, monitor and continuously improve. Cyber risk evolves constantly.
This structured approach supports essential eight cyber mitigation strategies and long-term resilience.

Supporting Education, Government, and Enterprise on Their Essential 8 Journey
Bluechip IT works with resellers, MSPs, and system integrators across Australia. We provide access to leading cybersecurity vendors aligned with the Essential eight acsc framework.
Our team supports:
- Solution Assessment
- Maturity alignment guidance
- Vendor solution mapping
- Local Australian expertise
We help partners deliver practical Essential eight security outcomes without overcomplicating the process.
Conclusion
The Essential 8 framework remains consistent across sectors. However, implementation is never one-size-fits-all. Education, government, and enterprise each face distinct risks. Therefore, each must align controls with operational impact and regulatory requirements.
With the right strategy and vendor ecosystem, Essential eight implementation becomes achievable and scalable.
Strengthen Your Essential 8 Strategy Today
Support your customers with sector-aligned Essential eight cyber solutions.
